Förderjahr 2025 / Stipendium Call #20 / ProjektID: 7820 / Projekt: Analyzing and Understanding the Internet of Insecure Things
Hybrid broadcast broadband TV (HbbTV) brings the web into our living rooms, but it also opens a hidden attack surface in millions of smart TVs.
What Is HbbTV and Why Should You Care?
Smart TVs have quietly evolved into small computers in our living rooms. They stream Netflix, run apps, listen for voice commands, and, in many countries, they also show web content on top of normal TV channels through standards like HbbTV (Hybrid Broadcast Broadband TV).
Our recent project took a deep look at how this web layer on TVs can be abused, and the results are… not great.
In many European countries (and parts of Asia and Oceania), TV channels can send a small "app URL" inside the broadcast signal. Your TV automatically opens that URL in a built-in HbbTV browser and overlays the content on top of the program you're watching.
That's how you get features like:
- Extra info during sports events
- Red-button services
- Interactive quizzes, shopping, or surveys
Under the hood, this is just a web app: HTML, CSS, JavaScript, plus some special TV-specific APIs to control channels, read device settings, or interact with remote control buttons.
And that's where things get dangerous.
How Attackers Can Hijack Your TV
We assume a realistic but powerful attacker: someone who can hijack the TV signal before it reaches your home (e.g., via cheap broadcasting equipment and an antenna or cable injection). This has been demonstrated to be feasible in previous work using off-the-shelf hardware.
Once they control the signal, they don't need to hack your Wi-Fi or install an app. They can simply:
- Replace the HbbTV app URL in the broadcast with their own malicious URL.
- Your TV, following the standard, loads that app automatically.
- Their code runs inside the HbbTV browser, often without any user interaction.
From there, we explored what a malicious app can actually do.
Four Types of Attacks
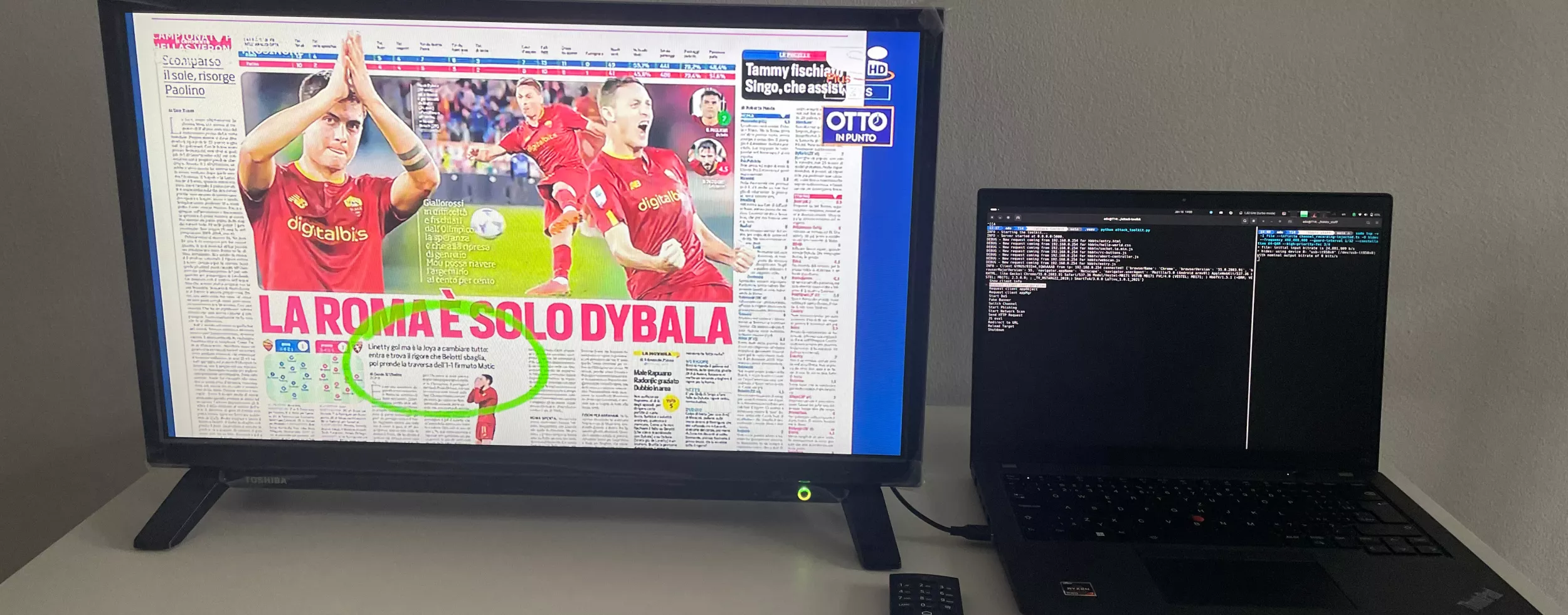
We built a modular "attack toolkit" and tested it on three Smart TVs from major vendors (Toshiba/Android TV, Samsung/Tizen, LG/webOS), manufactured between 2017 and 2024.
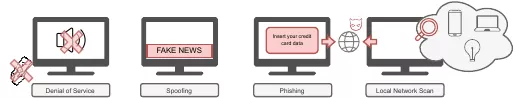
We showed four main attack classes:
1. Denial of Service (DoS) – Making Your TV Unusable
By abusing the HbbTV APIs and regular web features, an attacker can:
- Cover the whole screen with an image or message
- Play their own audio instead of the broadcast
- Capture most remote control buttons, so navigation stops working
- Force the TV to switch channels in a loop, hopping back and forth endlessly
Result: Your TV turns into a glitchy, locked-up box until you manage to regain control (often only by pressing the power button).
2. Spoofing – Spreading Misinformation
Because HbbTV apps can draw on top of live TV, an attacker can:
- Overlay a fake news ticker at the bottom of a news channel
- Replace parts of the video or audio with their own content
- Make it look like an official news channel is announcing false information
On some TVs, autoplay restrictions limited simple video replacement, but clever workarounds (e.g., embedded YouTube videos with autoplay) still allowed effective spoofing.
3. Phishing – Asking for Your Secrets on the Big Screen
Smart TVs often display pop-ups requesting logins, Wi-Fi passwords, or payment details. A malicious HbbTV app can mimic that look and:
- Display a fake prompt ("Your Wi-Fi password is required again" or a "payment" form)
- Accept input using the TV's on-screen keyboard
- Send the entered data back to the attacker's server
We didn't conduct user tests, but the phishing flow works end-to-end technically.
4. Local Network Reconnaissance – Using Your TV as a Pivot
On two of the three TVs, we were able to:
- Scan the local network from the TV (finding other devices at home)
- Send HTTP requests to those devices (e.g., routers, IoT gadgets, NAS, printers)
This turns your TV into a stealthy stepping stone for attacking your home network, often without anything visible happening on the screen. You'd only notice it by analysing network traffic.
The Root Cause: Frozen, Outdated TV Browsers
One of the most worrying findings is that HbbTV browsers are stuck in time.
- TVs typically do not update the HbbTV browser engine after launch.
- One device was still using a Chrome 55-based engine from 2016, with over 2,000 known vulnerabilities listed in public databases.
- Even when the TV's main firmware was updated (e.g., from Android 9 to Android 11), the HbbTV browser remained the same, and the attacks still worked.
In contrast, the separate "normal" browser you might install from the TV app store does get updates. The hidden, broadcast-only browser does not.
Across vendors, there were differences (newer Chrome on LG, older on Samsung, different HbbTV versions), but all TVs were vulnerable to most of the attacks.
What Needs to Change?
We argue that both standards bodies and manufacturers need to act:
- Enforce HTTPS by default for HbbTV apps, so injected plain-HTTP apps can't be loaded as easily.
- Treat the HbbTV browser as an updatable component, with regular security patches like any other browser.
- Introduce a permission model for sensitive features:
- Overriding remote control buttons
- Accessing the local network
- Integrating microphones, cameras, or voice assistants
- Add integrity checks (e.g., digital signatures) for HbbTV apps received via broadcast, so TVs only run authenticated content.
Until then, millions of hybrid-TV-enabled devices remain attractive targets.

