Förderjahr 2024 / Stipendium Call #19 / ProjektID: 7276 / Projekt: Attack Detection using Micro-architectural Traces and Machine Learning
When we talk about hackers, most people imagine someone cracking passwords or breaking into software. But there’s another kind of attack that doesn’t touch the software at all. Instead, it listens to the tiny “clues” a computer gives off while it’s w
Every computer chip, even the ones in your phone or laptop, leaks little hints about what it’s doing. It might draw slightly more power, take a fraction longer to finish a task, or leave behind tiny traces in its performance. To us, that looks like nothing. To an attacker, it can be a goldmine of secrets. Imagine someone learning your PIN code not by looking over your shoulder, but by watching how your hands move or listening to the clicks on your keypad. That’s the kind of trick a side-channel attack pulls using the “side effects” of computing to guess what’s really happening inside.
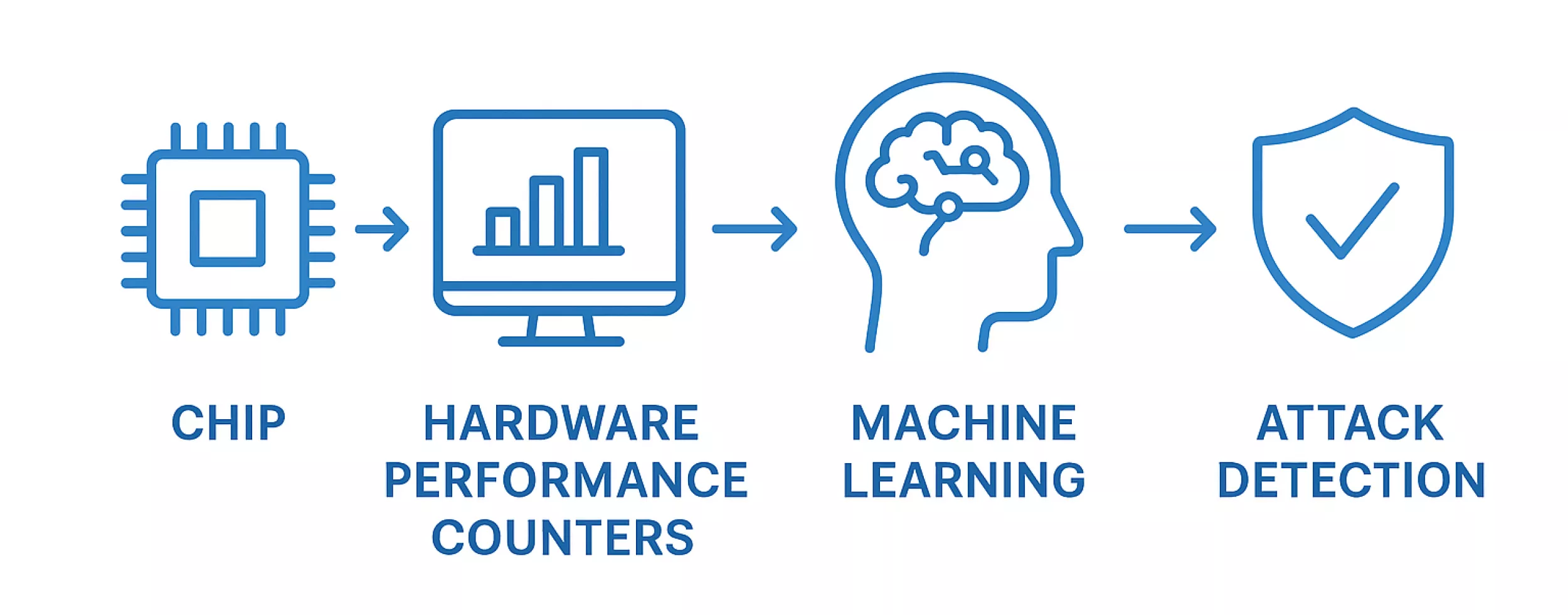
Why they’re hard to spot The problem is, these leaks don’t look dramatic. They blend in with the normal “noise” of a system. It’s like trying to notice a whisper in a busy café, you know it’s there, but it’s buried in everyday sounds. Traditional security tools usually miss it. The chip’s built-in diary, Here’s where something called hardware performance counters comes in. Think of them as a diary your processor keeps for itself. They quietly record what’s going on inside things like how many instructions were run or how memory was used. Alone, those notes don’t tell us much. But they’re rich with hidden details.
Machine learning as the detective Now imagine handing that diary to a really smart detective: machine learning. Instead of us trying to sift through all the messy details, machine learning can read the patterns, compare normal behavior with suspicious behavior, and spot the tiny differences that humans would miss. It’s like training your ear to recognize your best friend’s laugh in a crowded room. once you know the pattern, you can’t miss it.
Why we combine AI with hardware tools
 Hackers are creative. They keep inventing new ways to hide their tracks, and side-channel attacks are constantly evolving. That’s why we can’t just rely on fixed rules or old methods.
By combining artificial intelligence with hardware tools like performance counters, we create a defense system that can also evolve. Machine learning models can adapt as new attack strategies appear, learning from fresh data and staying sharp. In other words, we’re not just reacting to hackers—we’re aiming to stay one step ahead.
Hackers are creative. They keep inventing new ways to hide their tracks, and side-channel attacks are constantly evolving. That’s why we can’t just rely on fixed rules or old methods.
By combining artificial intelligence with hardware tools like performance counters, we create a defense system that can also evolve. Machine learning models can adapt as new attack strategies appear, learning from fresh data and staying sharp. In other words, we’re not just reacting to hackers—we’re aiming to stay one step ahead.
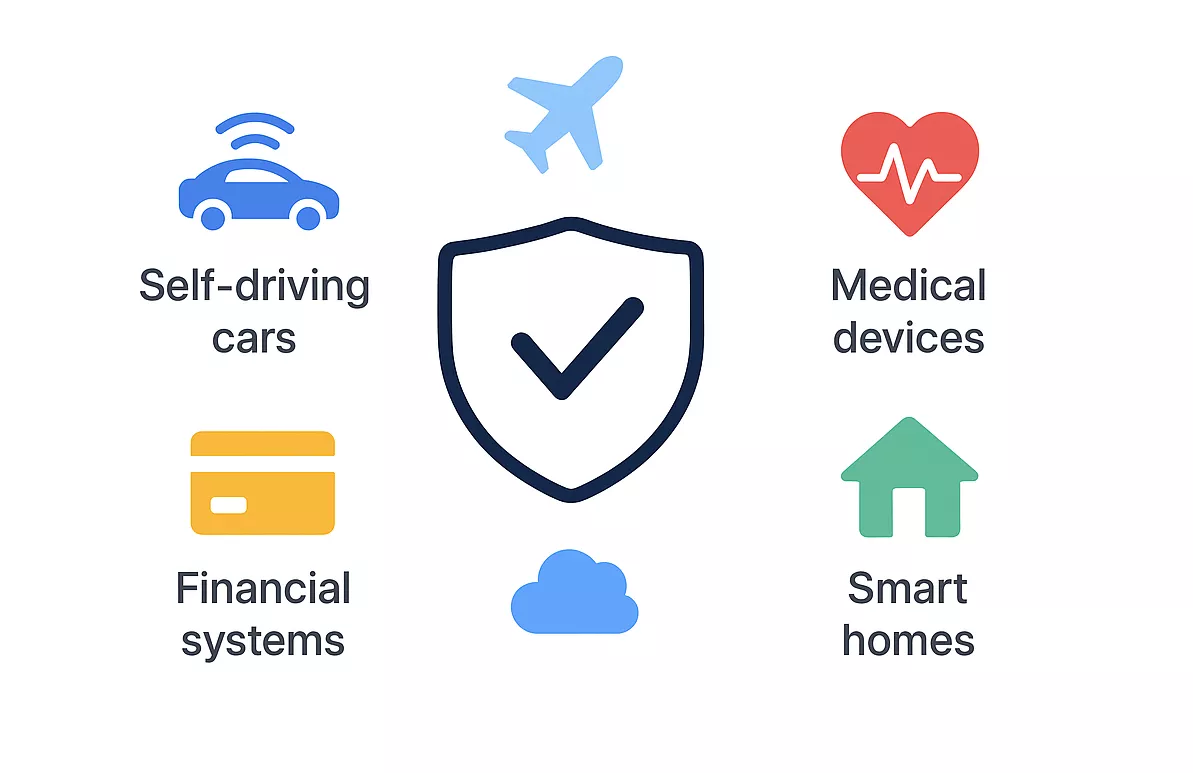
Real-world stakes: why it matters. Think about what’s at risk:
- Self-driving cars: Imagine hackers using a side-channel attack to peek into the system that decides when to brake or steer. A small leak could give them the power to manipulate the car’s decisions.
- Medical devices: Pacemakers and insulin pumps rely on secure chips. A leak here could allow someone to tamper with life-saving equipment.
- Smart homes: From door locks to security cameras, attackers could exploit hidden leaks to unlock your front door without ever touching the software.
- Financial systems: Even the encryption protecting your online banking could be weakened if side-channel clues are left unchecked.
This is why evolving defenses matter. Just like airport security updates to catch new smuggling tricks, our digital defenses must keep learning to spot the newest, most subtle attacks.
Our world runs on connected devices. By pairing AI with the hidden “diary” inside every processor, we gain a powerful, flexible way to guard against attacks that were once almost invisible.
We need to continue working toward smarter defenses, safer devices, and a digital world where security evolves at the same pace as emerging threats.