Förderjahr 2024 / Stipendium Call #19 / ProjektID: 7276 / Projekt: Attack Detection using Micro-architectural Traces and Machine Learning
This post outlines what makes our approach different, and why we believe this combination offers a powerful, efficient way to detect and understand emerging microarchitectural threats.
Most cyberattacks leave digital footprints such as logs, alerts, or suspicious activity you can track. But some attacks are much sneakier. They don't leave obvious signs in software. Instead, they exploit the way computer hardware works deep inside the system.
These are called side-channel attacks , and while they're quiet, they're not invisible.
How We Spot the Invisible
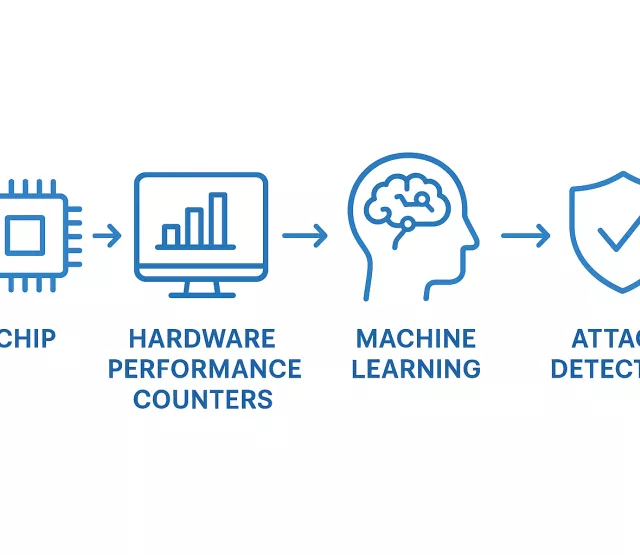
Even the stealthiest attack leaves behind small traces in the way your computer behaves, like tiny changes in how it uses memory or handles instructions. We tap into those traces using microarchitectural traces from hardware performance counters (HPCs), which are available in all modern processors that count things like missed memory accesses or unusual instruction flows and show patterns that help us detect unusual behaviors.
Our Method: Learning from Hardware Behavior
Instead of looking for only specific known attacks, our model learns how to distinguish between benign and attack processes. Here's how it works:
-
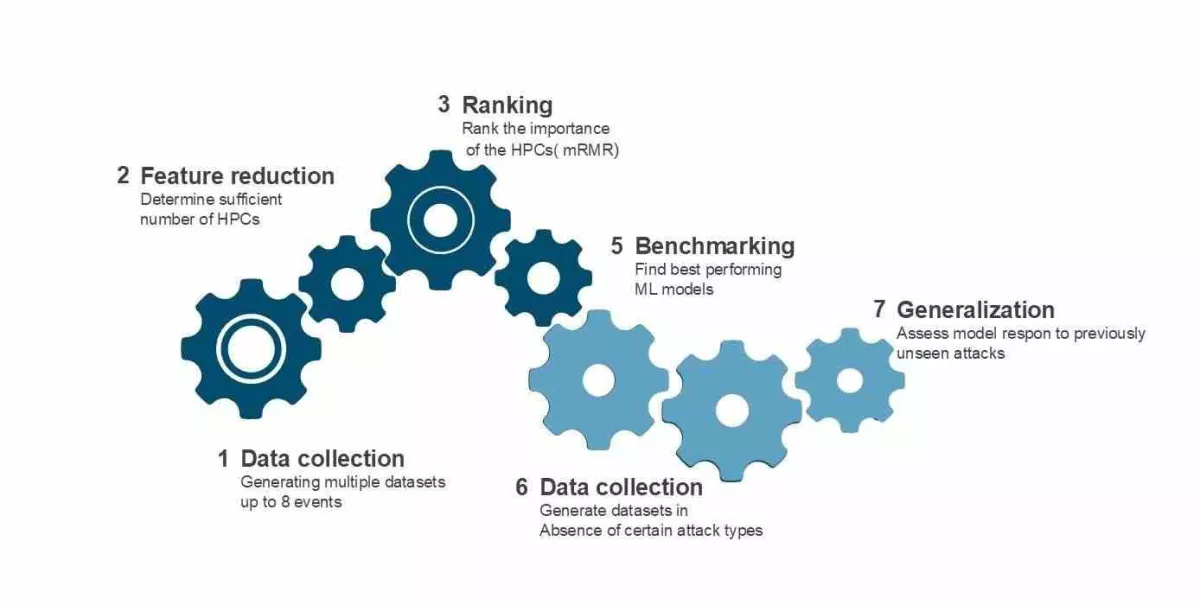
Collecting Data We captured hardware activity during both normal workloads ranging from light to intensive workloads and when simulated attacks happened in a controlled environment.
-
Finding the Right Traces We use statistics to find which hardware patterns are most useful in telling normal from abnormal behavior by selecting the best-performing hardware performance counters for the detection task.
-
Training Our Models With machine learning (including ensemble methods and deep learning), we train our model to recognize suspicious behavior in real-time.
-
Detecting Unknown Threats Because our system learns behavior—not specific attacks—it can even flag new types of threats that haven't been seen before.
Why This Matters
Cyber threats are evolving fast, and many go undetected by traditional tools. By paying attention to the hardware itself, we get an early detection model that catches what others miss.
If you're in cybersecurity, hardware development, or machine learning, we'd love to connect. The more perspectives, the stronger the defenses.
We're just getting started. Stay tuned; We'll be publishing detailed technical findings, datasets, and results from our model soon.