
Förderjahr 2025 / Projekt Call #20 / ProjektID: 7918 / Projekt: Sovereign SOC
The kubernetes SOC is a worldwide collaboration of leading eBPF projects in the cloudnative space. Copresenting how our ideas can be used in real life was rewarding and showcased the power of open source.
What we built as a first step
We combined three open-source projects to act as one unified security system:
-
Kubescape – learns what “normal” behavior looks like in an application.
-
Pixie – observes what applications actually do inside the cluster.
-
Clickhouse – stores detailed evidence when something suspicious happens.
Together, they outline a “prototypical SOC” (Security Operations Center) that runs completely inside the user’s own environment, even though it has two components: the sensors on each linux node and the central cockpit into which all data is collected.
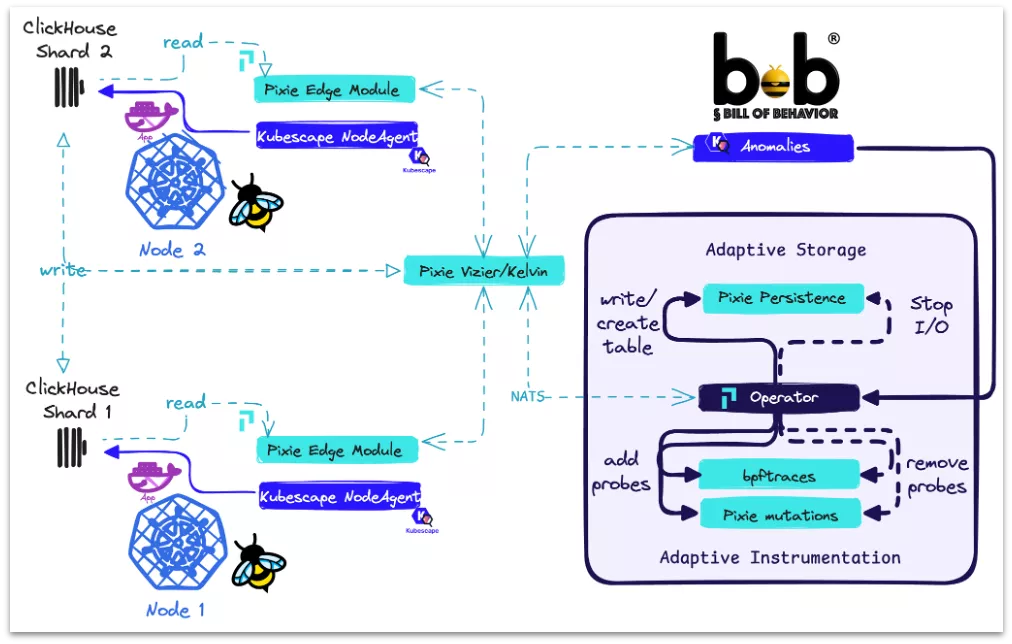
What the System Can Do
1. It learns normal behavior
The system automatically builds a profile of how each application normally behaves. This means it can notice when something suddenly changes—even if no one wrote a rule for it.
2. It detects suspicious behavior in real time
During the demonstration, we deliberately introduced a malicious software update into a test application. The system immediately noticed an unusual action that had never happened before. This early warning triggered the entire adaptive process.
3. It gathers evidence only when there are indicators of compromise
Instead of saving everything all the time, the system only collects detailed data when something suspicious occurs. This makes the system efficient and avoids unnecessary storage costs.
4. It zooms into the indicators adaptively
We used a "mock" compromised clickhouse application server, that gave us an initial "Indicator" in the form of a single system call. This, by itself, looked like it was just part of the rest of the software, but the adaptive data-gathering revealed that it was instead a very hard-to-detect io_uring rootkit. The individual adaptive eBPF probes revealed in the "zoom-in":
-
which internal service the compromised application contacted,
-
how often it reached out,
-
the unusual patterns in its network traffic,
-
and even some of the exact part of the malicious code: revealing that whatever was causing the anomaly must have been written in a totally different programming language.
-
the smoking gun evidence that this was highly malicious, was the detection of what the suspicous process was doing with the cache: it was reading tokens and sending them in some obscure binary format to a command-and-control server
Convince yourself in this free live online lab
https://labs.iximiuz.com/tutorials/musketkubecon-e3b29045
Why This Matters
Our demonstration showed that combining open-source tools creates a much stronger and clearer view of what is happening in a system. This “multimessenger” approach allows subtle attacks to be spotted quickly while keeping data sovereign and fully under user control.
Next steps
After showcasing the first time, how this combination of tools is more powerful than the sum of its parts, we now must build out the system to a functioning prototype
Learn more about the OpenSource Projects:
- https://github.com/kubescape
- https://github.com/k8sstormcenter
Constanze Roedig

