
Förderjahr 2020 / Stipendien Call #15 / ProjektID: 5294 / Projekt: Trustworthy Context-Aware Access Control in IoT Environments based on the Fog Computing Paradigm
Previously published blogs focus on the state-of-the-art within relevant software areas for my dissertation. As the dissertation closes to the finish line, the upcoming blog series will publish the design decisions and approaches I've taken to develop a trustworthy, context-aware access control solution for IoT. The first blog in the upcoming series deals with creating trustworthy IoT environments in the distributed Fog-based networks.
As presented in the previous blog - Managing trustworthy IoT environment [1], managing trust in computer networks heavily relies on mutual authentication. Mutual authentication often implies distributing security credentials (keys, password, certificates), which peers use to establish trust relationships. Credentials distribution is achieved through Key Management Protocols (KMP), which are utilized by trust models presented in the previously mentioned blog.
Despite having standardized and widely-applied trust models, their application in IoT is not straightforward due to the computational constraints of the IoT devices (sensors and actuators). For that reason, Fog Computing plays a significant role in offloading computationally intensive operations from IoT devices and establishing local trust domains at the IoT networks' edge. Through that, trust services are leveraged from Cloud Servers to local Fog networks.
Still, deploying trust services on Fog Nodes must adhere to the Fog Computing requirement that all Fog services must operate in offline scenarios, that is, without Cloud Server availability [2]. This requirement requires rethinking of the current trust models and KMPs.
Choosing trust model
Deciding between trust models required analysis against general IoT and the requirements mentioned above. The direct trust model implies peer-to-peer KMPs, introducing severe overhead in IoT networks due to their scalability and dynamicity. For that reason, utilizing only direct trust would be the wrong decision. Web of Trust (WoT) offers better scalability through somewhat centralized KMPs. However, credentials synchronization in WoT still fails to scale to fit IoT demands concerning its dynamicity (nodes joining or leaving the network). Moreover, having credentials shared through the whole WoT network implies nodes' availability, which contradicts Fog Computing requirements.
Hierarchical trust is a much better candidate since it enables following Cloud-Fog-Things hierarchy and decomposing trust management on multiple domains. This is achieved through transitive trust embedded in digital certificates signed by the trustworthy peer - often named Trust Anchor (TA) or Certificate Authority (CA).
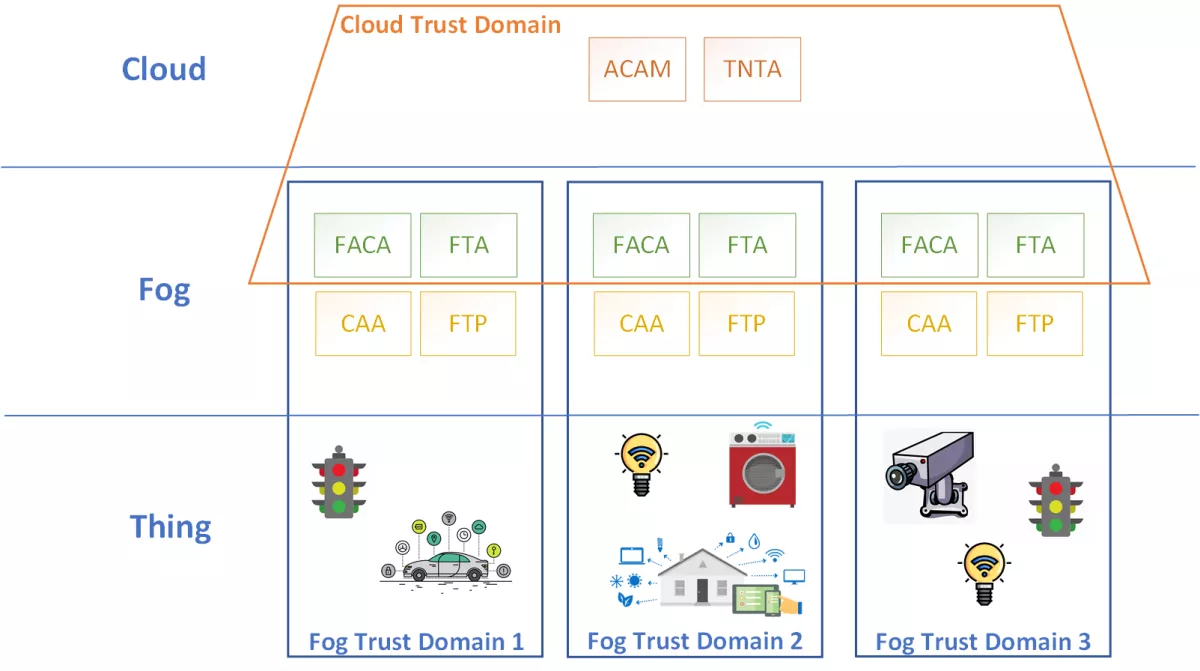
As presented in the figure, the designed solution distributes trust management from one Cloud to multiple Fog Trust Domains using hierarchical trust. These domains overlap in trust management software components:
- Trustworthy Networking Trust Anchor (TNTA) - CA for Cloud domain;
- Fog Trust Anchor (FTA) - CA for Fog Domain.
As TNTA is the root CA, its primary role is to manage certificates for FTAs. However, when TNTA is unavailable, FTA temporarily overtakes the root CA role for the Fog Domain. This is reflected in the FTAs certificate. Namely, if at any point in time FTA has reached TNTA, TNTA has issued the CA-signed certificate, valid in all trust domains. Otherwise, FTA temporarily issues itself a self-signed certificate valid only in a single Fog Trust Domain. The same public key pair is used both for self-signed and CA certificates, so changing the FTA certificate remains backward compatible.
Through this approach, the operability of the Fog Trust Domains is also maintained in "offline" scenarios. Each local network peer can be mutually authenticated, and its certificate can be validated against revocation. The minor drawback in the "offline" scenario is the inability to track the whole trust chain to TNTA due to the lack of network connection. However, since all operations are from authenticated peers in Fog Domain, their certificates can be fully validated when the connection to TNTA is re-established.
This blog covered the initial steps for trust distribution using Fog Nodes, describing trust model selection that supports requirements for developing the final solution. Based on the selected trust model, the next blog will provide further details on the designed KMPs - how are the digital certificates issued, validated, and revoked.
[2] OpenFog Reference Architecture for Fog Computing, URL: https://www.iiconsortium.org/pdf/OpenFog_Reference_Architecture_2_09_17.pdf


